Get Visibility Into Multi-cloud Security & Compliance Posture
Cyberthreat landscape is dynamically changing and new cyber risks emerge almost daily. Even after patching vulnerabilities, servers, workstations, server applications and more importantly IT assets with innumerable settings have to be properly configured to avoid data breaches. Accordingly, your vulnerability management strategy needs to expand.
Traditional Vulnerability Assessments Are Inadequate For Cloud
As we enter Cloud First era, it is futile to solely rely on routine assessments to prevent compromises. Organizations continue to struggle to achieve compliance and protect critical IT assets despite having a comprehensive vulnerability assessments program.
Traditional vulnerability assessments have several challenges:
Cloud Adoption and Risk Report 2019
14 misconfigured instances on an average at any given time resulting in 2,269 misconfiguration incidents in a month.
Study by Security Firm: Threat Stack
Three-quaters of all organizations on AWS are suffering some form cloud misconfiguration that impacts security.
McAfee Study
More than 5% of all AWS S3 Buckets in use today are misconfigured to be publicly readable.
Cloud Coverage
Coverage of cloud misconfigurations is one of the most prevalent and significant security risks facing organizations today. Studies reveal that configuration errors are triggering costly security breaches. However, most traditional assessments leave much to be desired for cloud-based assets.
Regulatory Compliance For Cloud Assets
Organizational need for regulatory compliance adherence requires audit. However, traditional assessments are manual, error prone and time consuming.
A truly comprehensive security controls posture is vital organizations.
Securing multi-cloud environment
Multi-cloud environment does offer a powerful combination of high resiliency and agility to the rapidly changing digital business needs. However, detecting and applying uniform security policies is now hygiene factor to take advantages of such an environment
Traditional assessment approaches come up short on this goal.
Gain Visibility. Augment Your Assessment Program.
Switch to Automatic Multi-Cloud Assessment
The first step towards effective cloud security is to recognize the significance of configuration.
Keeping track of configuration changes in a multi-cloud environment and adhering to regulatory compliances all the time is truly an overwhelming task. Most organizations that try to audit their cloud infrastructure rely upon checklists, spreadsheets and manual reviews. Today, organizations can have an automated and continuous configuration and compliance assessment to keep track of any changes.
Automate Assessments with CloudOptics Assessment and Advisory
CloudOptics, Assessment and Advisory Solution provides actionable insights into your entire infrastructure security risks allowing you to quickly identify, investigate, prioritize and remediate vulnerabilities across cloud environments.
Why CloudOptics Assessment & Advisory?
- Cloud-based solution. No deployment costs and complexity of legacy configuration management products anymore.
CloudOptics lets you perform configuration assessments quickly and comprehensively. Just sign up and add your existing Cloud assets. The entire configuration posture is available in a single pane of glass for a holistic view. Some of such important features of CloudOptics are.
End to end Visibility
End to End Visibility for a continuous visibility of all cloud assets
Compliance Control Assessment
Get immediate & accurate status of your ISO 27001, PCI DSS, HIPAA, NIST CSF etc., across clouds
Ultimate Convenience
Zero touch assessment & reporting, ease of use through self-service intuitive interface
Actionable Insight
Actionable insights with in-depth summary & detailed report, enables control failure visibility to specific asset configuration
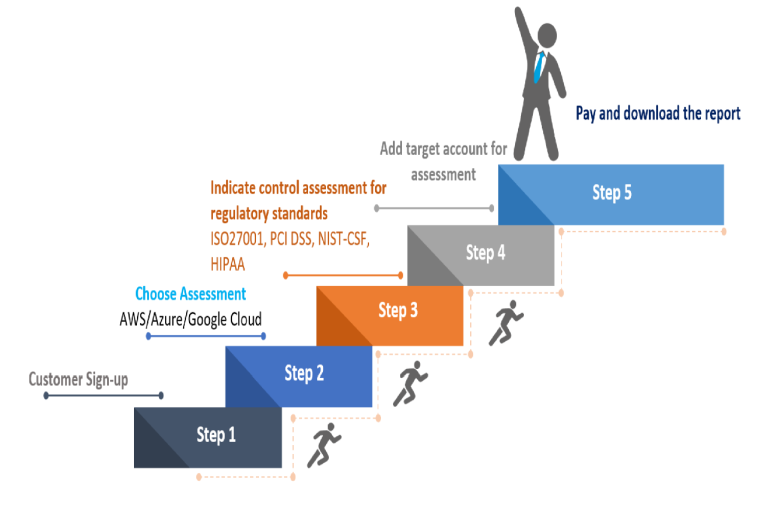
How It Works?
CloudOptics provides a simple and intuitive web-based user interface. Businesses can schedule assessments, automatically create downloadable reports of issues and view dashboards.
Sign up and enhance your vulnerability management program in 5 easy steps.